Practice good online safety habits with these tips and advice.
1. Keep a clean machine
- Have the latest security software – malware (virus, e.t.c.) keep evolving each day. Having the latest security software is the best defense against these malware.
- Automate software updates – On a personal machine this is the best practice, especially on Windows. But in a corporate environment, automatic updates on a production machine are not encouraged. It is best to first test the updates on a separate machine in case they break anything. If they are successful you can then apply them on the production server.
- Protect all devices that connect to the internet – All computers, smartphones, gaming systems and other web-enabled devices also need protection from viruses and malware.
- Plug and Scan – USBs and other external devices can be infected by viruses and malware. Use your security software to scan them before opening them on your machine.
2. Protect your personal Information
- Lock Down Your Login – Fortify your online accounts by enabling the strongest authentication tools available, such as biometrics, security keys or a unique one-time code through an app on your mobile device. Your usernames and passwords are not enough to protect key accounts like email, banking and social media.
- Make your password a sentence – A strong password is a sentence that is at least 12 characters long. Focus on positive sentences or phrases that you like to think about and are easy to remember (for example, “I love country music.”). On many sites, you can even use spaces!
- Unique account, unique password – Having separate passwords for every account helps to thwart cybercriminals. At a minimum, separate your work and personal accounts and make sure that your critical accounts have the strongest passwords.
- Write it down and keep it safe – Everyone can forget a password. Keep a list that’s stored in a safe, secure place away from your computer. You can alternatively use a service like a password manager to keep track of your passwords.
3. Connect with care
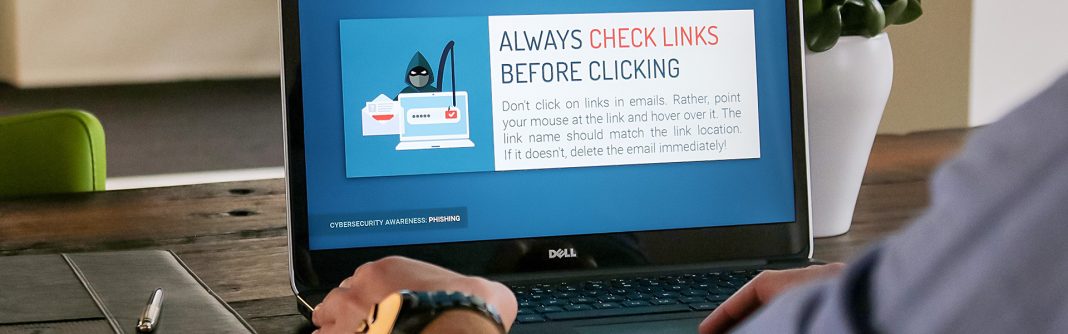
- When in doubt, throw it out – Links in emails, social media posts and online advertising are often how cybercriminals try to steal your personal information. Even if you know the source, if something looks suspicious, delete it.
- Get savvy about Wi-Fi hotspots – Limit the type of business you conduct using the so favorite ‘hotspots’ and adjust the security settings on your device to limit who can access your machine.
- Protect your $$ – When banking and shopping, check to be sure the site is security enabled. Look for web addresses with “https://” or “shttp://,” which means the site takes extra measures to help secure your information. “http://” is not secure.
4. Be web wise
- Stay current – Keep pace with new ways to stay safe online: Check trusted websites for the latest information, and share with friends, family, and colleagues and encourage them to be web wise.
- Think before you act – Be wary of communications that implore you to act immediately, offer something that sounds too good to be true or ask for personal information.
- Back it up: – Protect your valuable work, music, photos and other digital information by making an electronic copy and storing it safely.
5. Be a good online citizen
- Safer for me, more secure for all – What you do online has the potential to affect everyone – at home, at work and around the world. Practicing good online habits benefits the global digital community.
- Post only about others as you have them post about you. The Golden Rule applies online as well.
- Help the authorities fight cybercrime – Report stolen finances or identities and other cybercrime to the Internet Crime Complaint Center (www.ic3.gov) and to your local law enforcement or state attorney general as appropriate.
6. Own your online presence
- Personal information is like money. Value it. Protect it. Information about you, such as your purchase history or location, has value – just like money. Be thoughtful about who gets that information and how it’s collected through apps and websites.
- Be aware of what’s being shared. Set the privacy and security settings on web services and devices to your comfort level for information sharing. It’s OK to limit how and with whom you share information.
- Share with care – Think before posting about yourself and others online. Consider what a post reveals, who might see it and how it could be perceived now and in the future.